Reverse Engineering Signatus.exe (bmdyy) - Part 2
Continuing the second part of my reverse engineering the signatus.exe bmddy.
If you haven’t followed the first part, click here Reverse Engineering Signatus.exe (bmdyy) - Part 1
If you already read this 2nd part, the full poc I developed can be looked at my github repository Signatus.exe (bmdyy) - Exploit Dev POC
As discussed on part 1, we have to get a successful condition at jz instruction at 0x60AE13E5 memory address which compares the result of encrypt_timing_func + additional calculation against first 4 bytes of our payload, I already developed a function in Part-1 that will address this issue.
Next we need to continue our reverse engineering analysis, a message is printed to the console saying "> correct ODT received.".
The sofware will make a call to WS2_32!recv and receive the next 4 bytes in our payload. Again after the call completes its compared against the returned value stored in eax against 0x0FFFFFFFFh (-1), the WS2_32!recv returns -1 if no data is received, if received, it returns the number of bytes received and store it in eax register.
Next branch (0x60AE142C) will compare eax with 0x4, will jump to successful branch(red color) if the value is equal, otherwise will jump to unsuccessful (green arrow) and the program will print the failed message and continue to look for new incoming data.
The program will take the succesful branch as we have data for the second 4 bytes. we should focus on function call 0x60AE1470 and I renamed in IDA Free to func_opcodes_analyze (0x60AE1470).
The function will use the payload value at offset 0x8 in the payload as an opcode value that will be compared against multiple values and will perform an action if the opcode value matches.
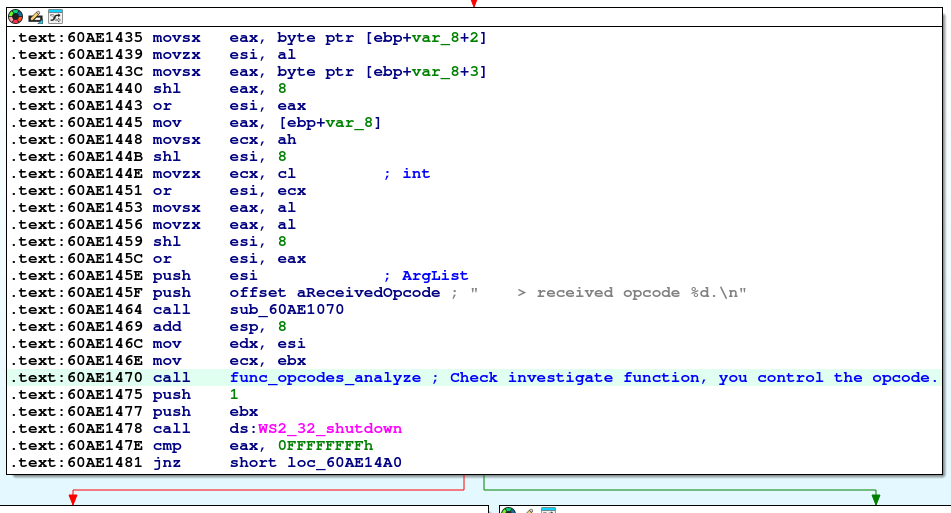
After reverse engineering the function I named to func_opcodes_analyze (0x60AE1470).
I discovered the following valid opcodes:
Signatus available Opcodes
- 0x1 (0x60AE1107) -> Will append payload data to the file: c:\Users\Public\signatus.log
- 0x2 (0x60AE11DB) -> Will read payload data from the file c:\Users\Public\signatus.log
- 0x3 (0x60AE12A9) -> Will write payload data to the file c:\Users\Public\signatus.log
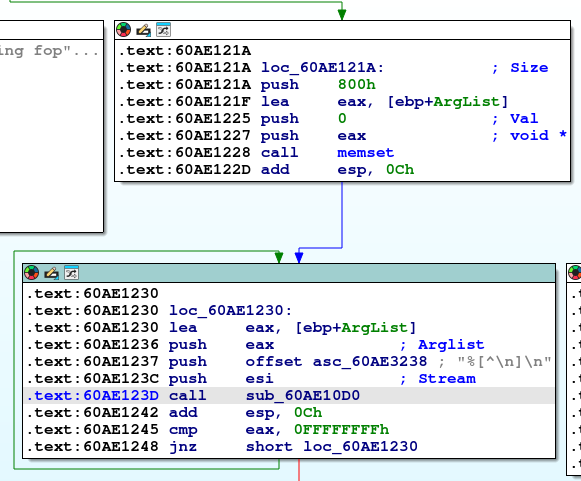
The out of bounds buffer memory corruption happens in the vfscanf function when reading data back from the file into the buffer, there is no size check before reading the data from the file which causes the program to write data beyond the buffer.
To trigger the vulnerability the following has to happen:
- Write to a file two times with large data using 0x1 opcode.
- Trigger a read operation by using 0x2 opcode instructing the program to read the data in the file back to program’s buffer
Following the action above we will be able to overwrite SEH (Structure Exception Handler) and control EIP. The vulnerable function is located in the memory address 0x61AE123D